We have seen an increasing number of reports for business email compromise affecting organisations, so we are calling on everyone not to be an April fool!
“Business email compromise” is a where a hacker gains access to a corporate email account by pretending to be a figure such as a business owner, manager or other decision maker to defraud the organisations or its employees, customers or suppliers of money.
Whilst these scams targeted businesses working with suppliers and businesses that regularly make electronic payments in the past, small businesses and not-for-profit organisations are no longer immune.
We are aware of several cases where a business owner was compromised through a fake email which included a link to download a file from SharePoint or Google Drive location.
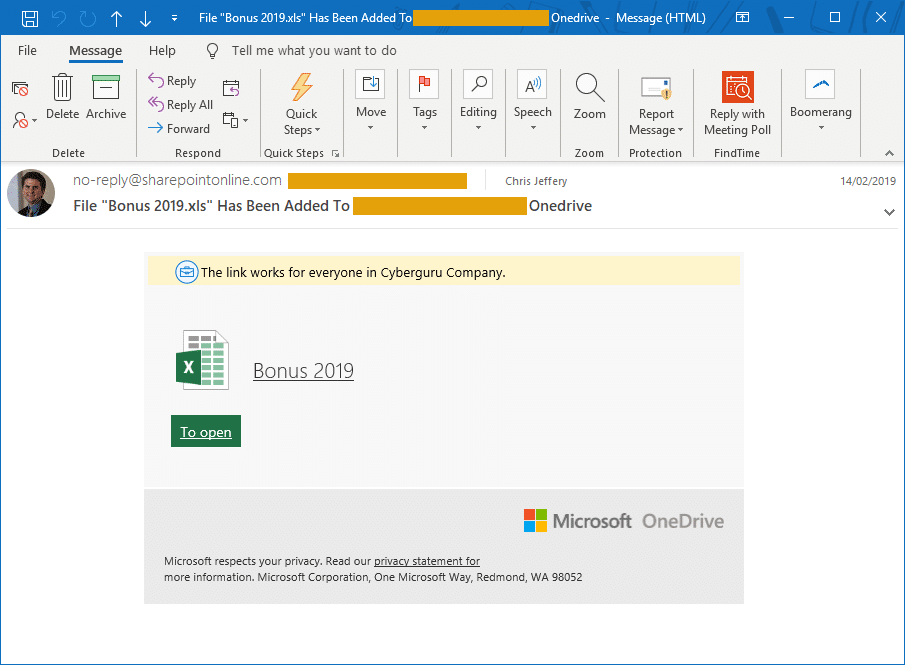
In order to download the file, the owner was required to login to what appeared to be a genuine Microsoft or Google sign in page, but was actually fake. Once the account details were entered they were saved and sent to the hacker.
The hacker then used these details to log in and review the contents of the business owner’s email, often accessing their email or address book, to identify contacts from their business, and use their email to send a compromised email to either the accounts department or the business’s clients.

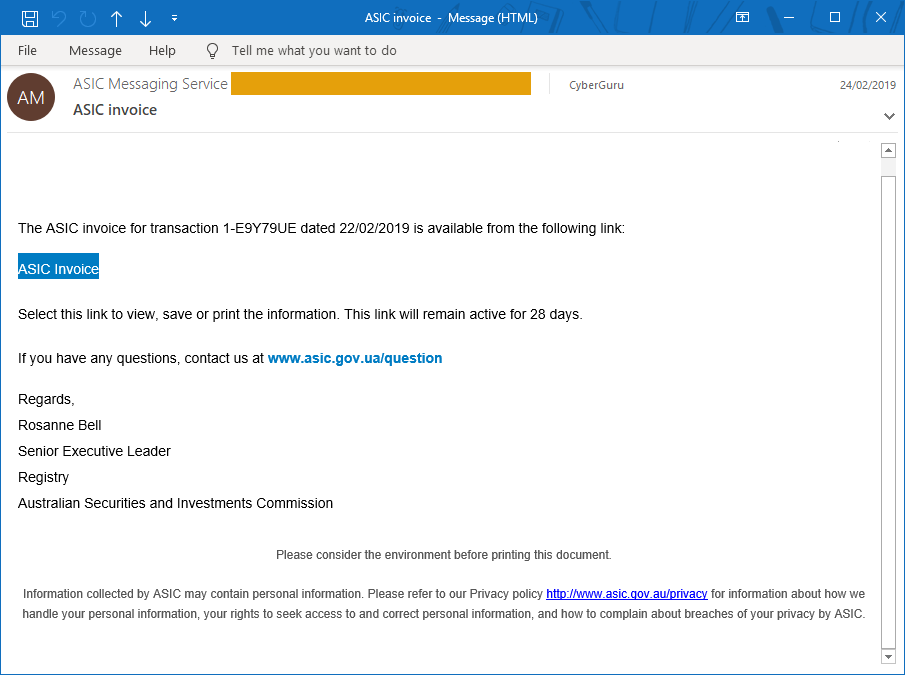
The emails sent to accounts and/or clients contain a fictious invoice requesting payment or another fake link to a Microsoft or Google login page as well, then both the CEO and accounts have been compromised.
In some cases, once the scammer had control of the email account used they set up rules to forward incoming email to an external email address of the hacker, automatically delete all email coming the inbox and remove the contents of the current inbox altogether so the account holder was unaware the new email had ever been received.
To protect yourself from such scams, we strongly suggest reviewing your protection strategies including staff education and training before you are compromised. If you receive an email from someone and are required to login to access a document or invoice and you weren’t expecting it, call the sender to confirm it is legitimate. It is important to quickly get onto it.
CyberGuru provides a range of services including consulting, support and training to protect against cyber threats such as these. If we can be of assistance, please contact us.


