As noted in our blog post in February, we wished to provide an update on the email authentication changes brought in by Google and Yahoo. Over the past few months, we have worked with many clients to ensure to the delivery of the email to reduce the likelihood and impact of the cause of this. […]
Tag Archives: Google
You might have seen recent announcements about crucial enhancements and requirements aimed at bolstering email security and ensuring successful delivery to Google and Yahoo email addresses. These changes are designed to refine the email authentication process, safeguard against spam, and verify the authenticity of senders. The key components of these changes involve the implementation of […]
Google has recently announced that legacy G Suite free edition will no longer be available from 1 July 2022. Google G Suite free edition was originally available for businesses and schools, some 16 years ago, however Google has now advised that it requires its clients to transition all remaining users to an upgraded Google Workspace […]
Google Chrome has been in the news over the past few weeks, and not all the reporting has been entirely accurate. So, what’s fact and what’s fiction? Here we answer a few common questions that have come up as a result of various media reports and social media commentary. Did Google really advise users […]
In this month’s Ask CyberGuru we are asked, “I have moved onto a cloud-based service thinking that by moving onto this that it is backed up, but understand from talking to others that I need to back up. Is this the case?” When you move onto the cloud, you may not realise that cloud-based vendors […]
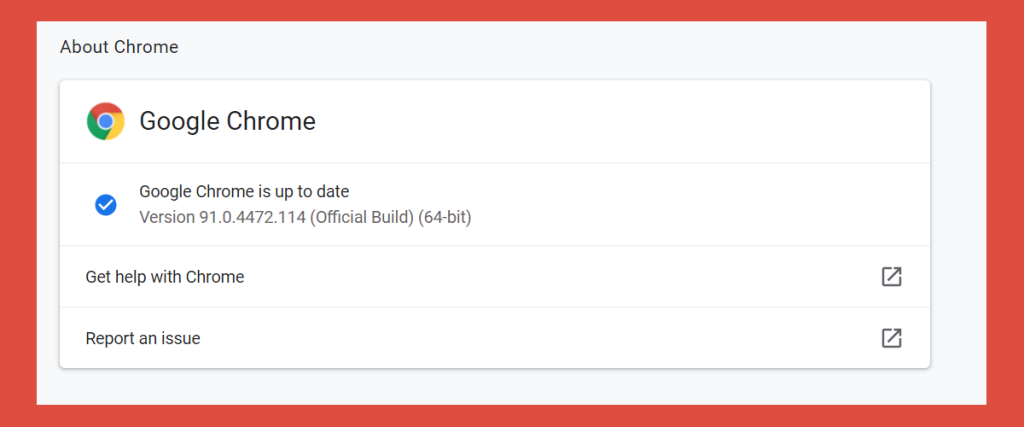
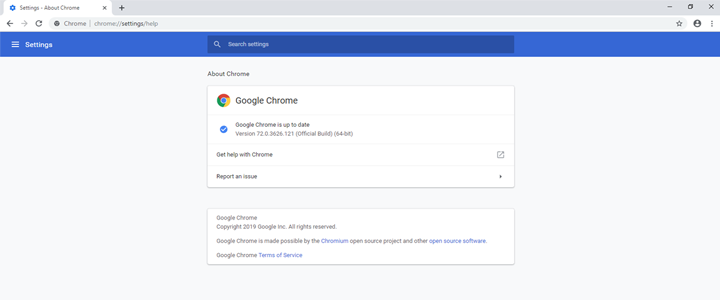
Google has released critical security updates for all Google Chrome users on Windows, Mac and Linux desktops and laptops. These security updates to address two security vulnerabilities on 17 June 2021. If these updates are not applied then hackers could exploit the vulnerabilities to gain access to your device. CyberGuru’s managed services clients will receive […]
Written by Jessie Jeffery, Business Development Guru, CyberGuru A recent landmark ruling by the Federal court finding for the Australian Competition and Consumer Commission (ACCC) in its case against Google means companies can no longer hide behind their privacy policies. In summary, the court found Google had misled Google account users about the whether their […]
Over the past few weeks, we have seen a number of outages affecting various internet service and cloud-based providers across the world. These have resulted in downtime, loss of productivity and frustration from the inability to conduct normal business activities. Our reliance on available, secure and reliable services has certainly come to head during COVID-19. […]
In this month’s Ask CyberGuru, we are asked, “I have received an email advising me that Google is closing down on 2 April, is this true?”. We have had a number of clients and family members check in with us regarding the closure of Google. It is in fact Google+ which is closing down, not […]
On Friday 1 March, Google announced it had discovered a Zero-Day Vulnerability “CVE-2019-5786” in its Google Chrome browser. It’s time to update your Google Chrome browser! Whilst only limited details have been published on the Chrome Releases blog, it is strongly suggested that you update Google Chrome if you are using this as your browser. […]
- 1
- 2